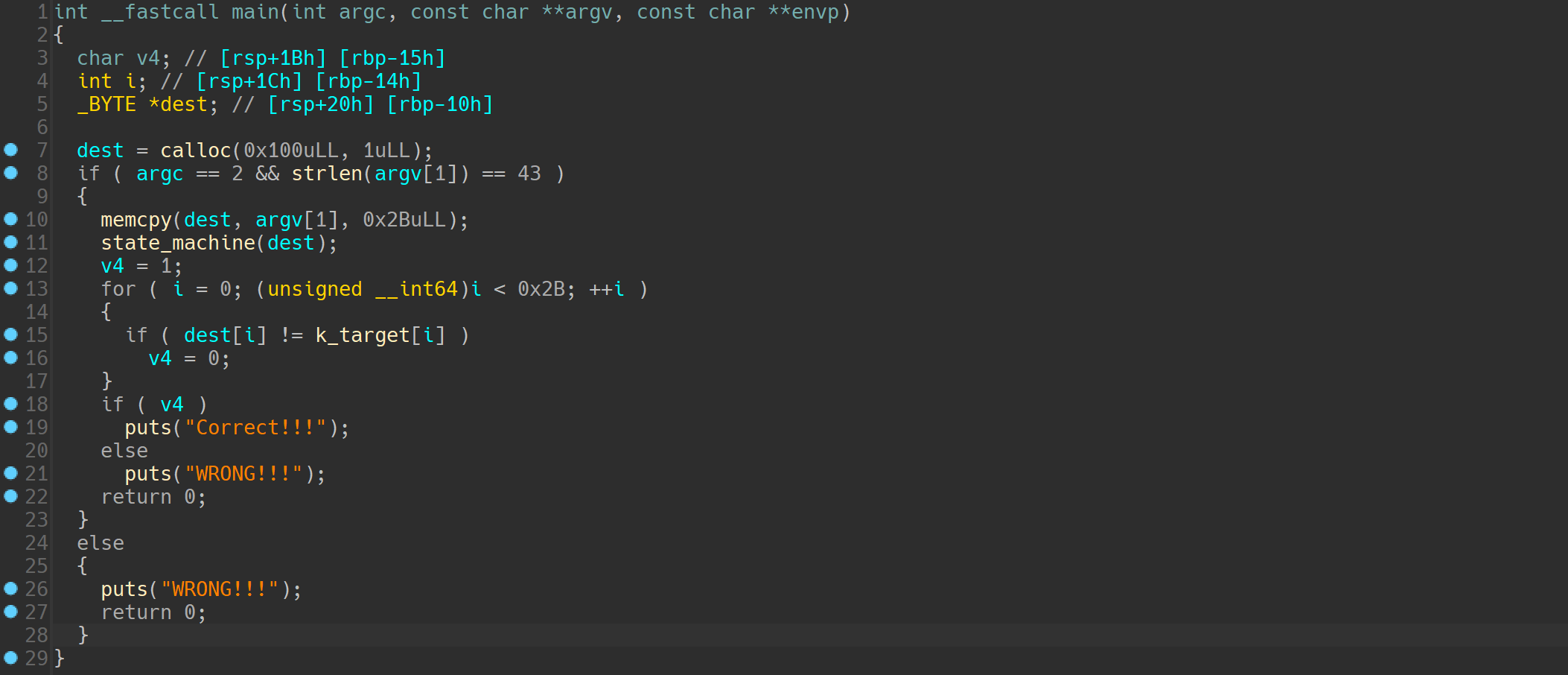
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| a1 = [15, 119, 236, 51, 68, 22, 19, 89, 29, 66, 132, 117, 95, 228, 131, 192, 59, 193, 149, 207, 219, 51, 108, 210, 237,
114, 95, 13, 116, 65, 91, 115, 160, 51, 83, 36, 2, 89, 116, 96, 51, 204, 125]
a1[5] -= a1[37] + a1[20]
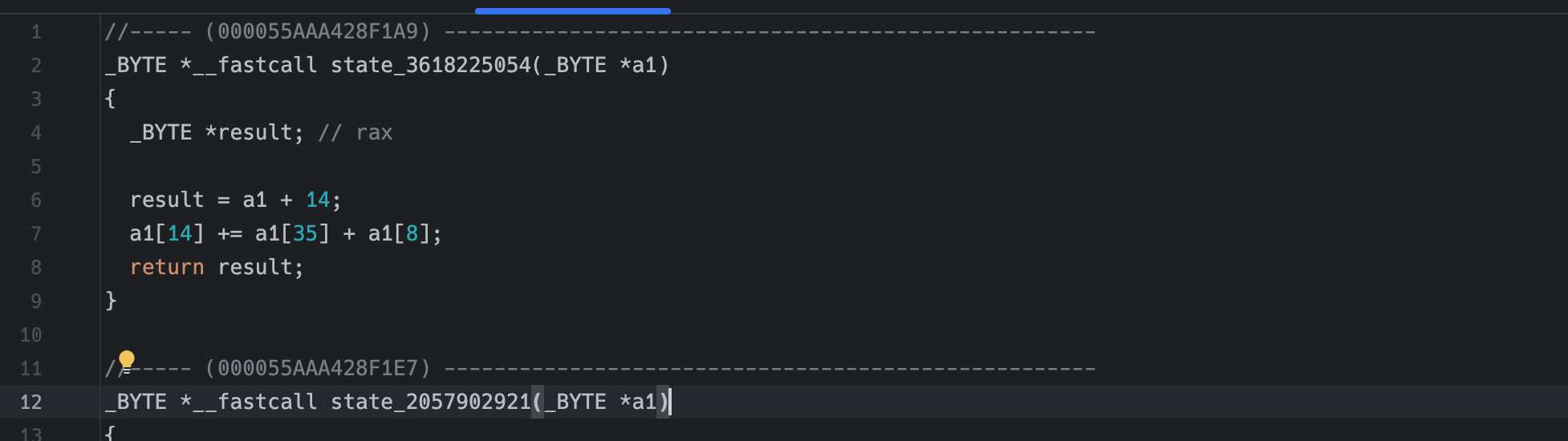
a1[8] -= a1[14] + a1[16]
a1[17] -= a1[38] + a1[24]
a1[15] -= a1[40] + a1[8]
a1[37] -= a1[12] + a1[16]
a1[4] -= a1[6] + a1[22]
a1[10] += a1[12] + a1[22]
a1[18] -= a1[26] + a1[31]
a1[23] -= a1[30] + a1[39]
a1[4] -= a1[27] + a1[25]
a1[37] -= a1[27] + a1[18]
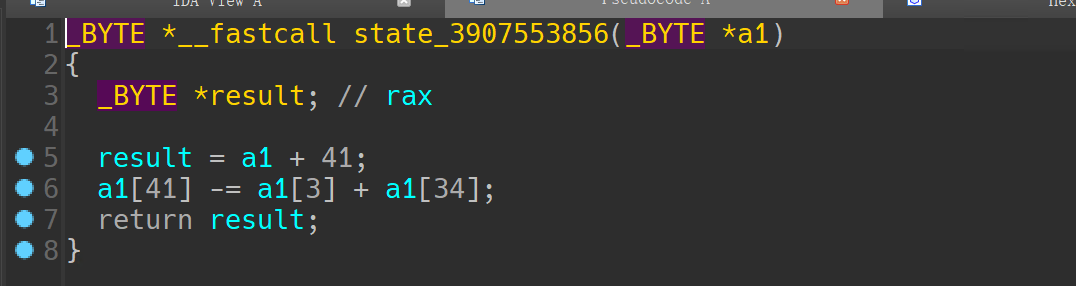
a1[41] += a1[3] + a1[34]
a1[13] -= a1[26] + a1[8]
a1[2] -= a1[34] + a1[25]
a1[0] -= a1[28] + a1[31]
a1[4] -= a1[7] + a1[25]
a1[18] -= a1[29] + a1[15]
a1[21] += a1[13] + a1[42]
a1[21] -= a1[34] + a1[15]
a1[7] -= a1[10] + a1[0]
a1[13] -= a1[25] + a1[28]
a1[32] -= a1[5] + a1[25]
a1[31] -= a1[1] + a1[16]
a1[1] -= a1[16] + a1[40]
a1[30] += a1[13] + a1[2]
a1[1] -= a1[15] + a1[6]
a1[7] -= a1[21] + a1[0]
a1[24] -= a1[20] + a1[5]
a1[36] -= a1[11] + a1[15]
a1[0] -= a1[33] + a1[16]
a1[19] -= a1[10] + a1[16]
a1[1] += a1[29] + a1[13]
a1[30] += a1[33] + a1[8]
a1[15] -= a1[22] + a1[10]
a1[20] -= a1[19] + a1[24]
a1[27] -= a1[18] + a1[20]
a1[39] += a1[25] + a1[38]
a1[23] -= a1[7] + a1[34]
a1[37] += a1[29] + a1[3]
a1[5] -= a1[40] + a1[4]
a1[17] -= a1[0] + a1[7]
a1[9] -= a1[11] + a1[3]
a1[31] -= a1[34] + a1[16]
a1[16] -= a1[25] + a1[11]
a1[14] += a1[32] + a1[6]
a1[6] -= a1[10] + a1[41]
a1[2] -= a1[11] + a1[8]
a1[0] += a1[18] + a1[31]
a1[9] += a1[2] + a1[22]
a1[14] -= a1[35] + a1[8]
for i in a1:
print(chr(i & 0xff), end='')
|