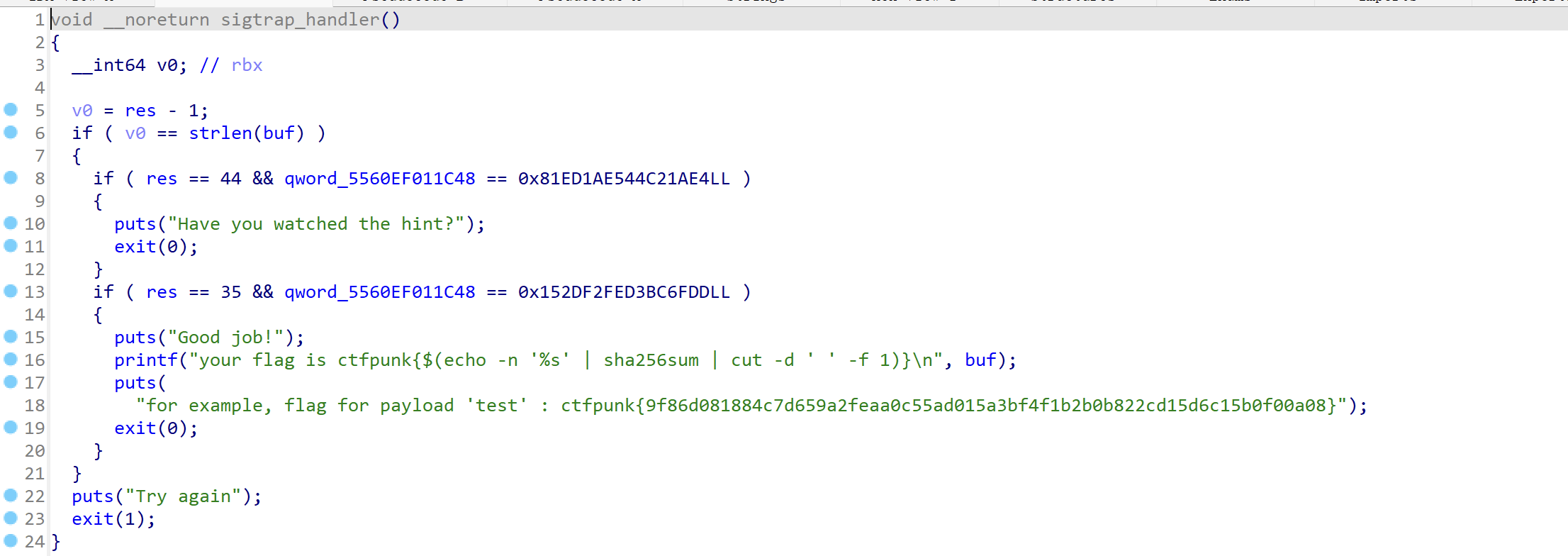
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
| from ctypes import c_uint64
mem = [0x0, 0x2bf4933a1cb3b58e, 0x7443445b968d2dda, 0x24d81331ab93926b, 0xedb9a55a2706e7f1, 0x3b29a6ca60076d30,
0xf02a50dd94c6794c, 0x788397af131ae243, 0x4592198be422b199, 0xd0e49650aafe2a0b, 0xc3f2e8a8b76b4b5e,
0xf4680e5b38eb45f0, 0x9737184f4b5fc4fa, 0x3b6f79dd0fe28a91, 0xa1aadc7345ec7461, 0x2e704e6598ad8b3c,
0x16771f41b5c1641b, 123, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0,
0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0,
0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0]
def add(argv, argc):
argv[0] += 2
argv[1 + ((argc >> 16) & 0x3f)] = c_uint64(argv[((argc >> 8) & 63) + 1] + argv[((argc & 0x3F) + 1)]).value
def sub(argv, argc):
argv[0] += 2
argv[1 + ((argc >> 16) & 0x3f)] = c_uint64(argv[((argc & 0x3F) + 1)] - argv[((argc >> 8) & 63) + 1]).value
def xor(argv, argc):
argv[0] += 2
argv[1 + ((argc >> 16) & 0x3f)] = c_uint64(argv[((argc >> 8) & 63) + 1] ^ argv[((argc & 0x3F) + 1)]).value
def sub_5950(argv, argc):
argv[0] += 2
if argv[((argc >> 8) & 63) + 1] == argv[((argc & 0x3F) + 1)]:
argv[1 + ((argc >> 16) & 0x3f)] = 1
else:
argv[1 + ((argc >> 16) & 0x3f)] = 0
def sub_59e0(argv, argc):
argv[0] += 2
if c_uint64(argv[(argc & 63) + 1]).value > c_uint64(argv[(((argc >> 8) & 0x3F) + 1)]).value:
argv[1 + ((argc >> 16) & 0x3f)] = 1
else:
argv[1 + ((argc >> 16) & 0x3f)] = 0
def sub_5a90(argv, argc):
result = argc & 0x3f
argv[0] += 2
if argv[result + 1] != 0:
argv[0] = argc >> 8
def func_table_3():
add(mem, 0x101000)
add(mem, 0x101001)
sub(mem, 0x101002)
add(mem, 0x101003)
add(mem, 0x101004)
xor(mem, 0x101005)
sub(mem, 0x101006)
add(mem, 0x101007)
xor(mem, 0x101008)
sub(mem, 0x101009)
add(mem, 0x10100a)
sub(mem, 0x10100b)
add(mem, 0x10100c)
sub(mem, 0x10100d)
sub(mem, 0x10100e)
add(mem, 0x10100f)
print(mem[17])
func_table_3()
|