2023NewStar-Reverser-Android(all)
Last updated on March 31, 2024 pm
复现一下以前的没做安卓题,顺便加深新学的知识
Week2
AndroGenshin
静态分析手撕即可,RC4+Base64
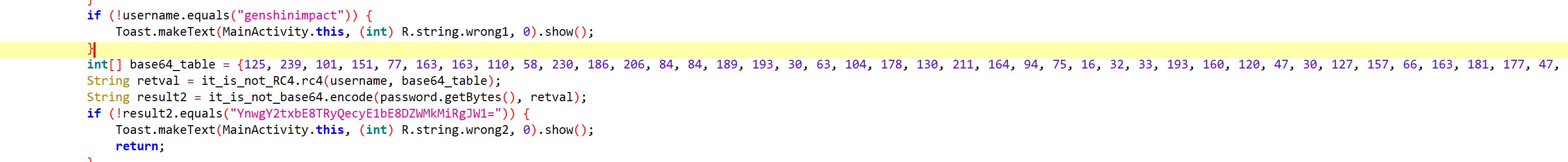
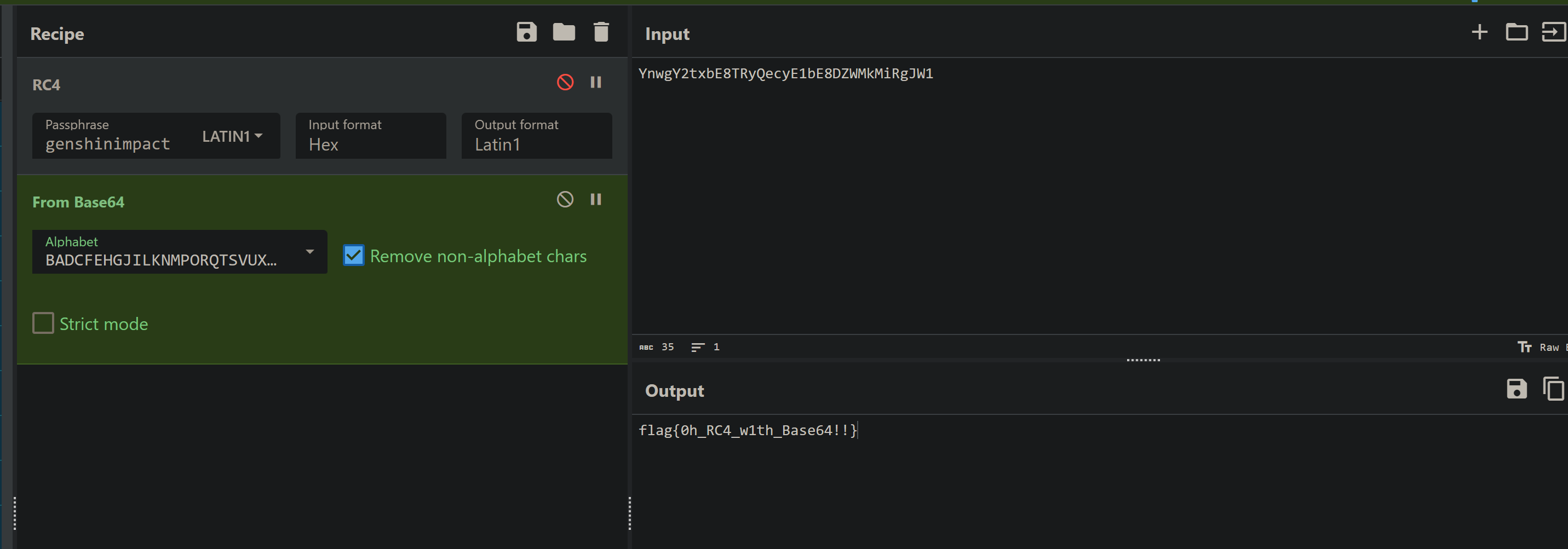
AndroDbgMe
直接使用MT管理完成更改以及重签名
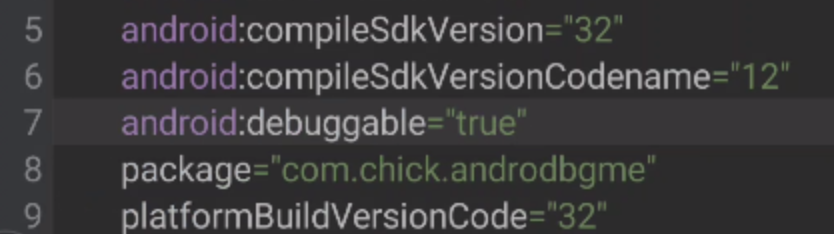
命令adb shell am start -D -n com.chick.androdbgme/.MainActivity调试模式启动,然后Jadx或者Jeb连上即可

Week3
Andronative
native方法检验,转去so看
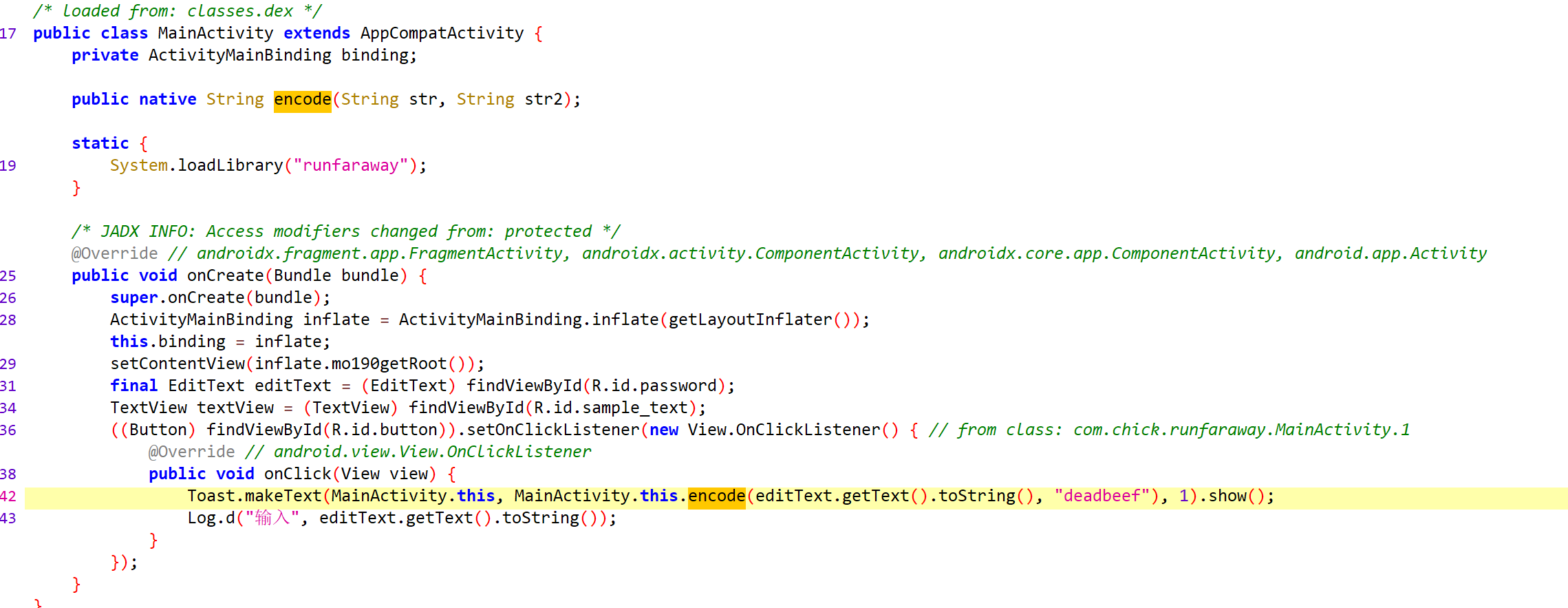
很容易找到关键的地方
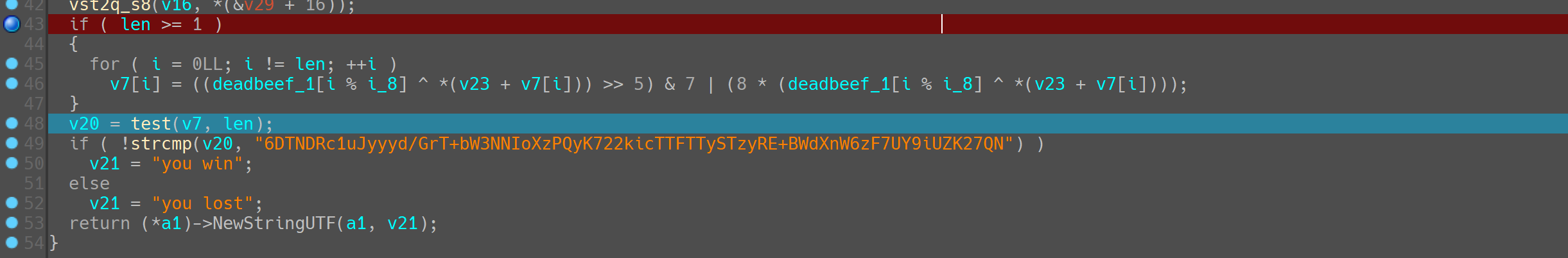
下断点调试,看汇编会轻松一点
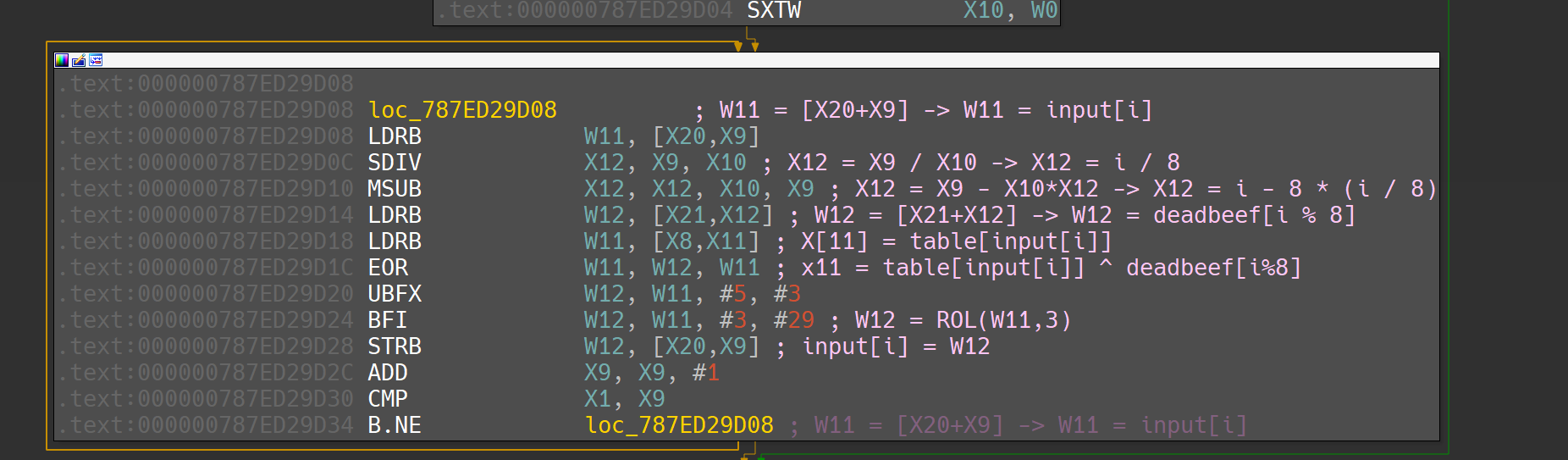
转为对应python代码如下
1 | |
再走完这个加密后,又走了一个变表的base64,接下来就很容易搓逆脚本了
1 | |
2hard2u
一个Java层面的控制流混淆,控制点是str的值。
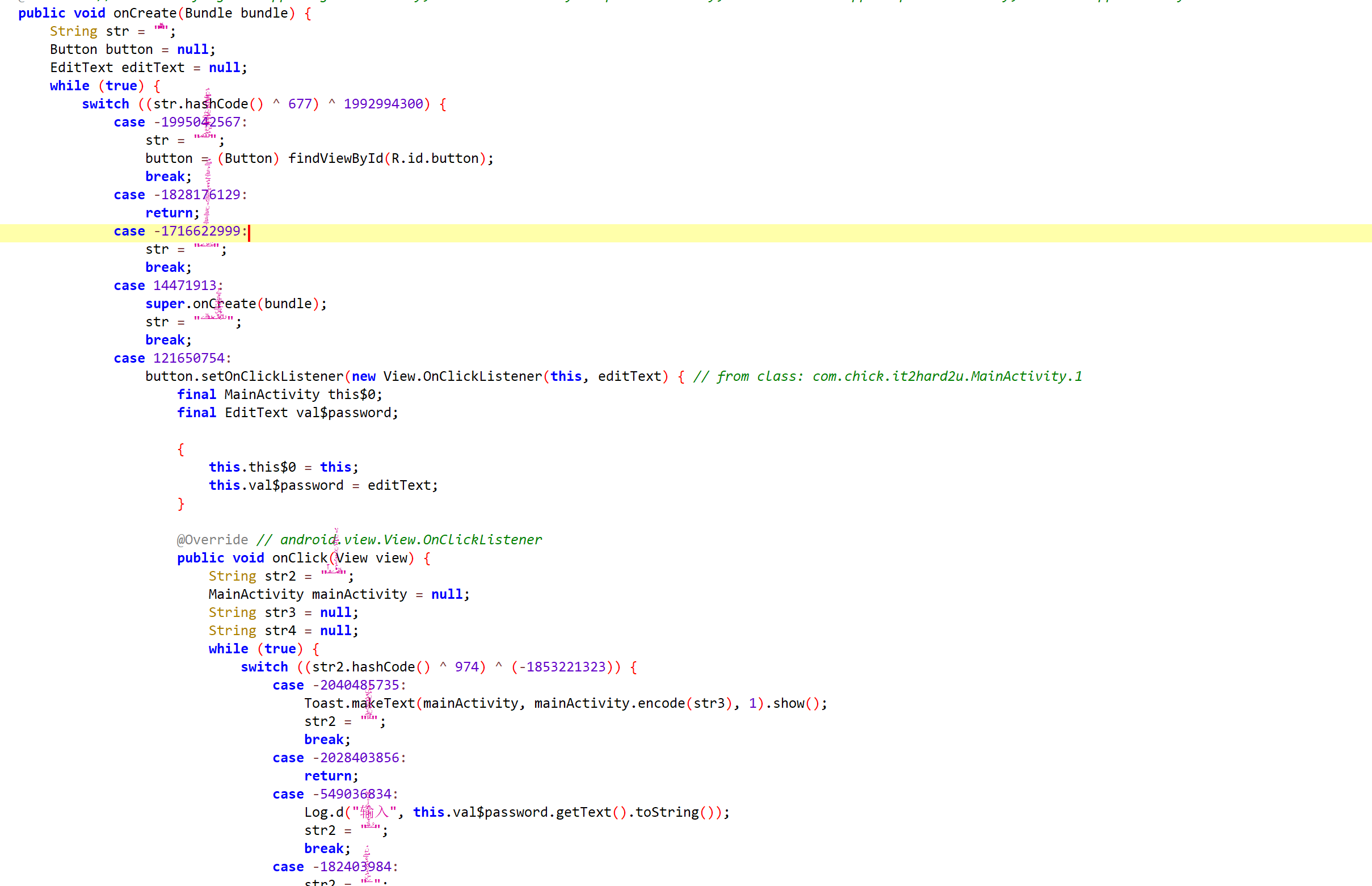
一般控制流呼混淆基本思路都是恢复控制流,找到真实的控制流是怎么样。这里最笨的思路就是手动提取,因为这里str的值自始至终都是与用户无关,即控制流是基本确定的,可以用python啥的脚本提一提,然后再分析。这里采取ZenTracer来查看控制流。
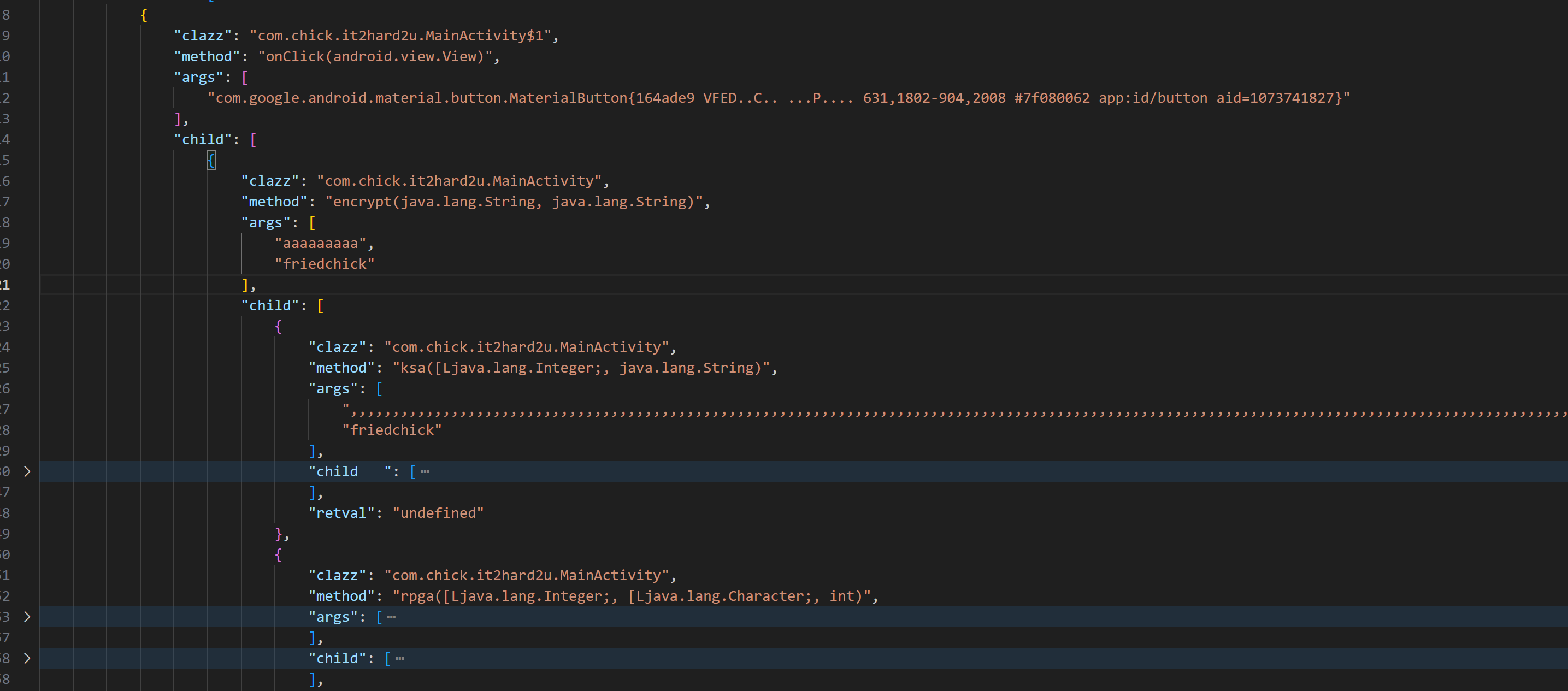
大致的控制流就是
onClick -> encrypt -> ksa 、 rpga
JAVA层
其中encrypt的参数是输入和friedchick,这里先跟入ksa查看,可以发现ksa里面调用了很多次swap函数,而且经过观察swap的第二个参数是从0~255递增的。
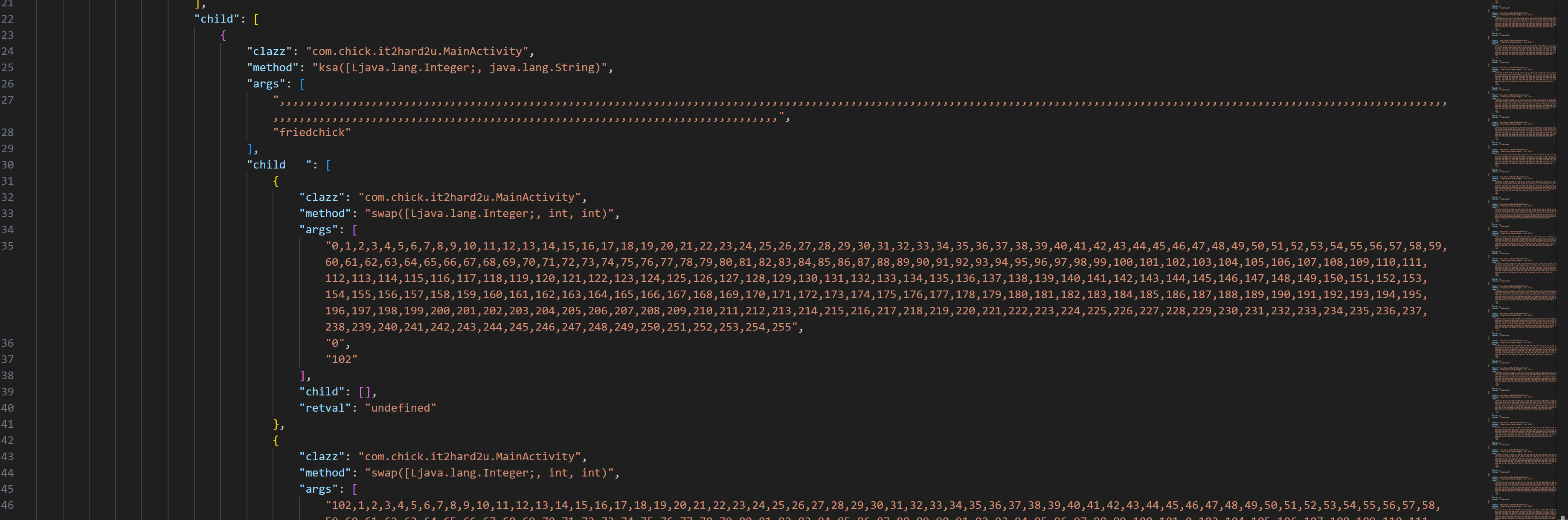
不妨简单看一下swap的java代码
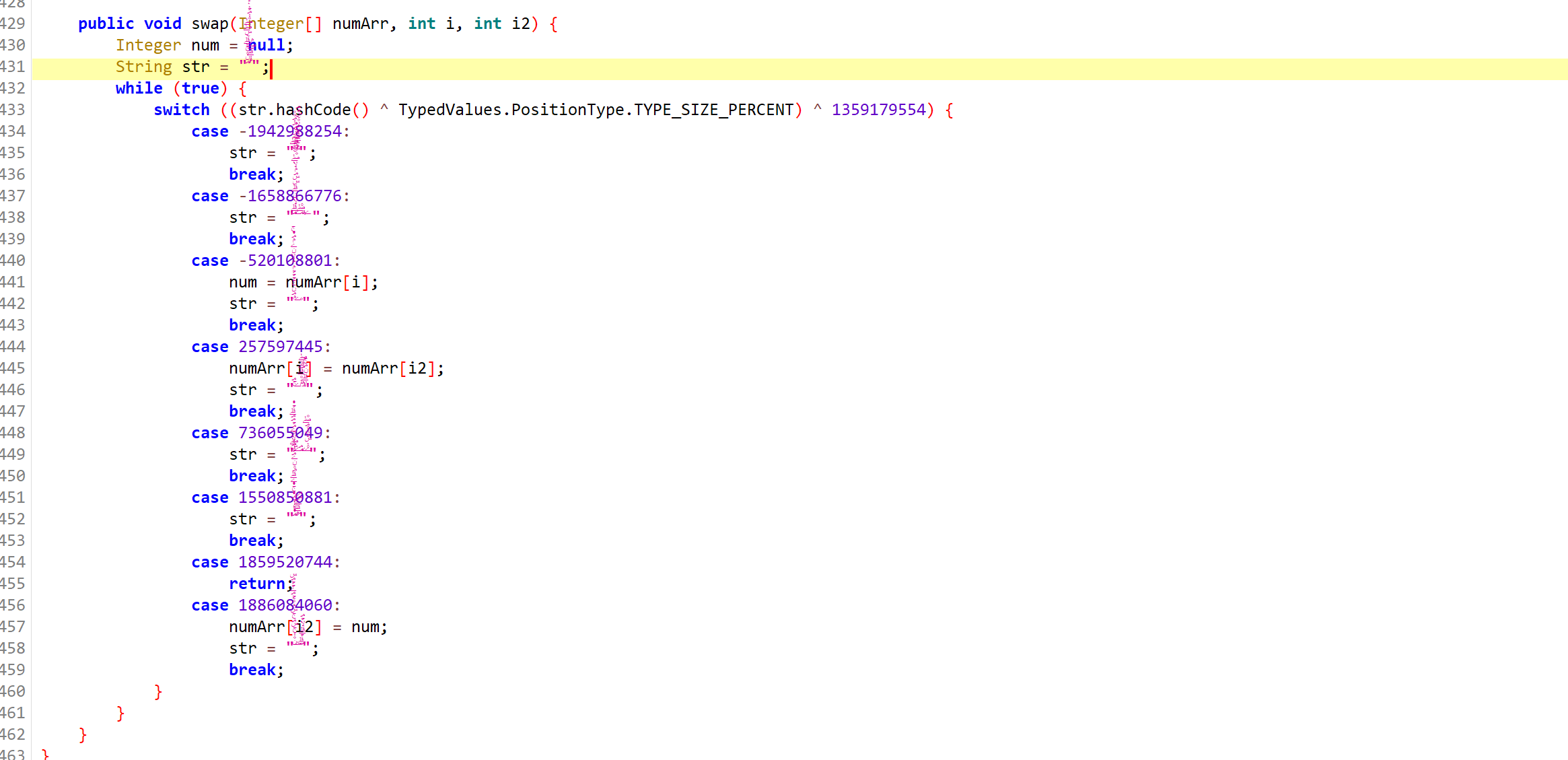
大致也能看出来是交换数组numArr的值,参数2、参数3就是要交换的坐标
即 numArr[i], numArr[i2] = numArr[i2], numArr[i],这里交换了256次。其实有点经验的话,可以知道这就是RC4的准备部分,即打乱S盒。
继续往后看rpga
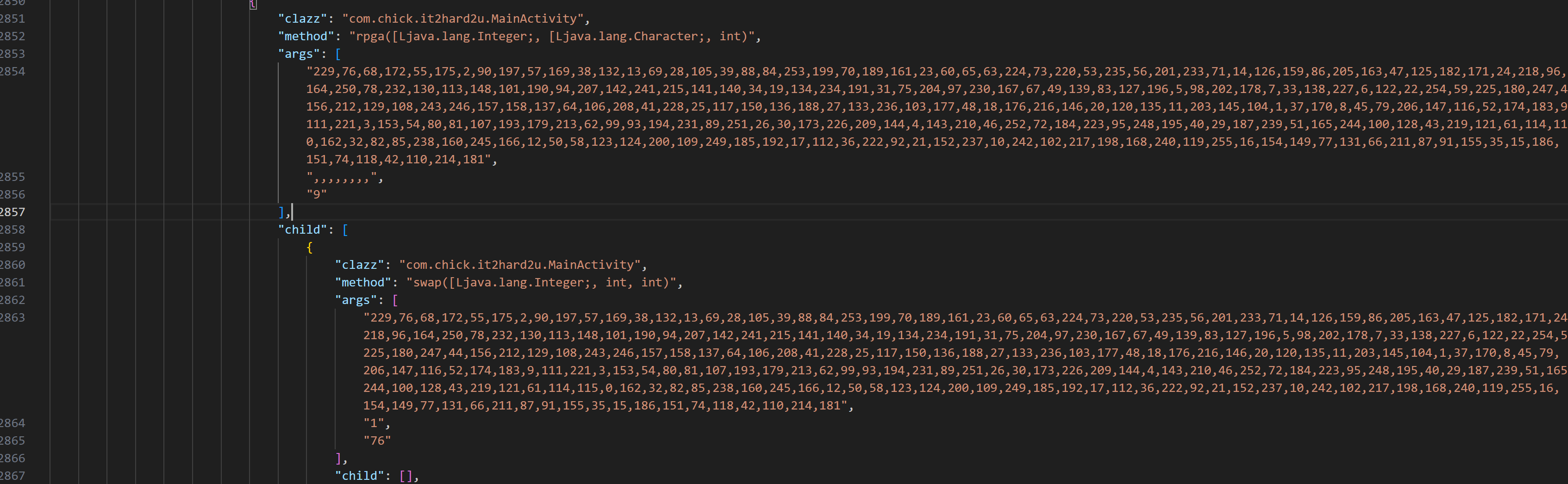
这里也是一堆的swap操作,不过不同的是这里只执行了9次,结合输入只有9个字符,可以猜测出这里应该是生产密钥流。通过最后的返回值也可以看到,只有九个字符
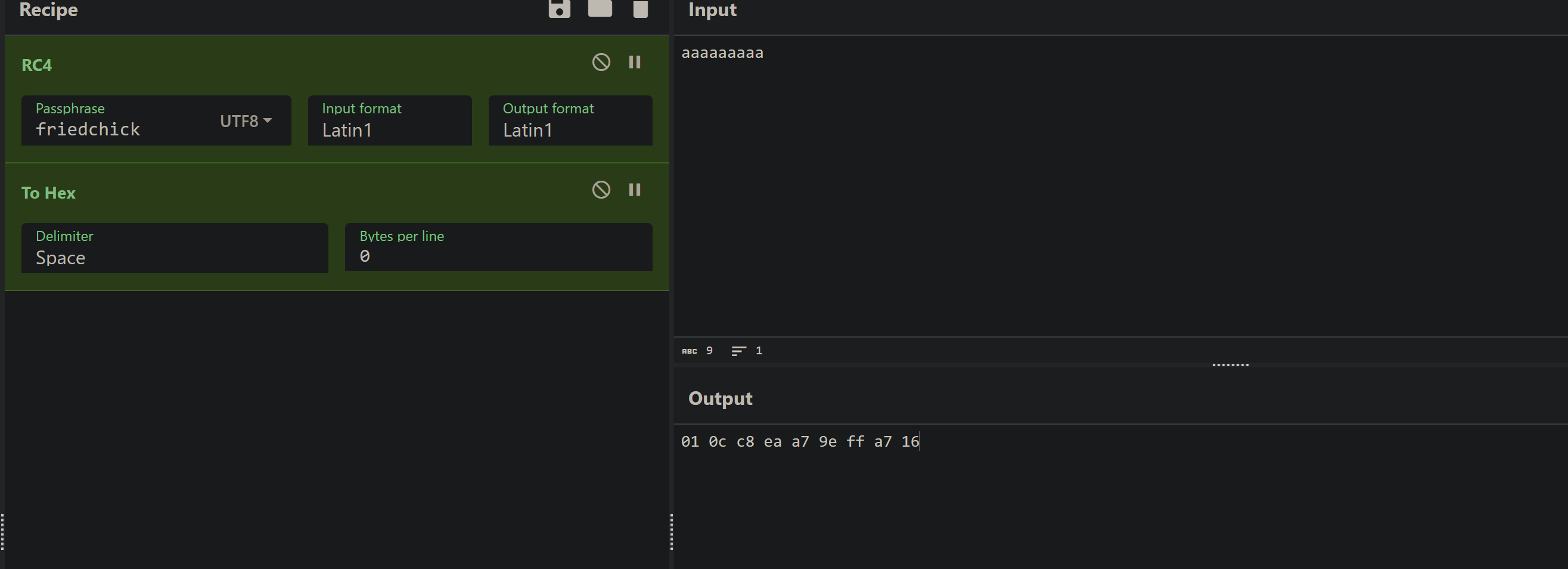
与CyberChef对比,基本一致
So层
继续往后看就是So里面的encode方法,直接IDA打开看
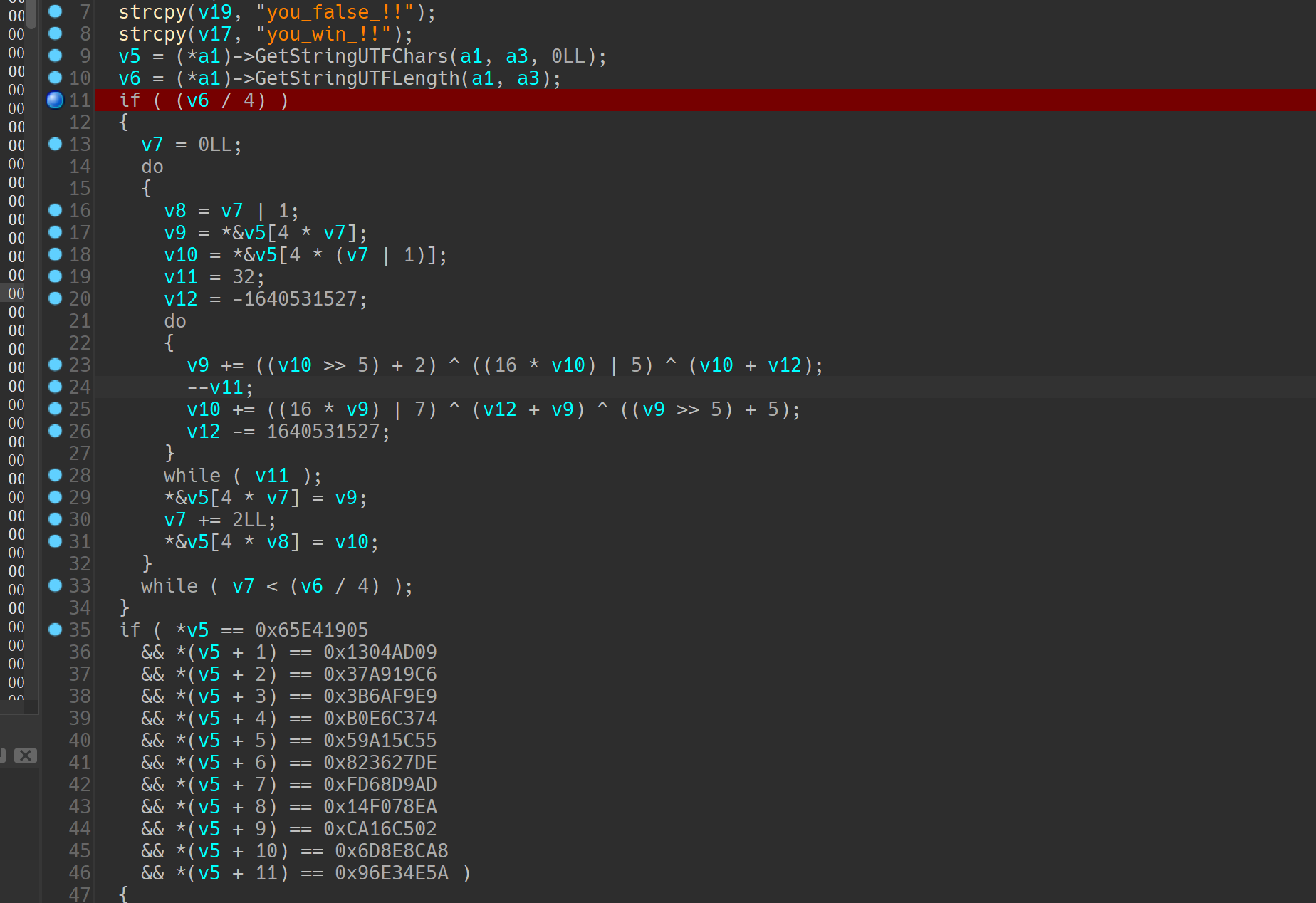
很容易看出这就是一个TEA加密
简单的搓个逆脚本
1 | |
然后还需要转换一下,从C的char*转回utf-8
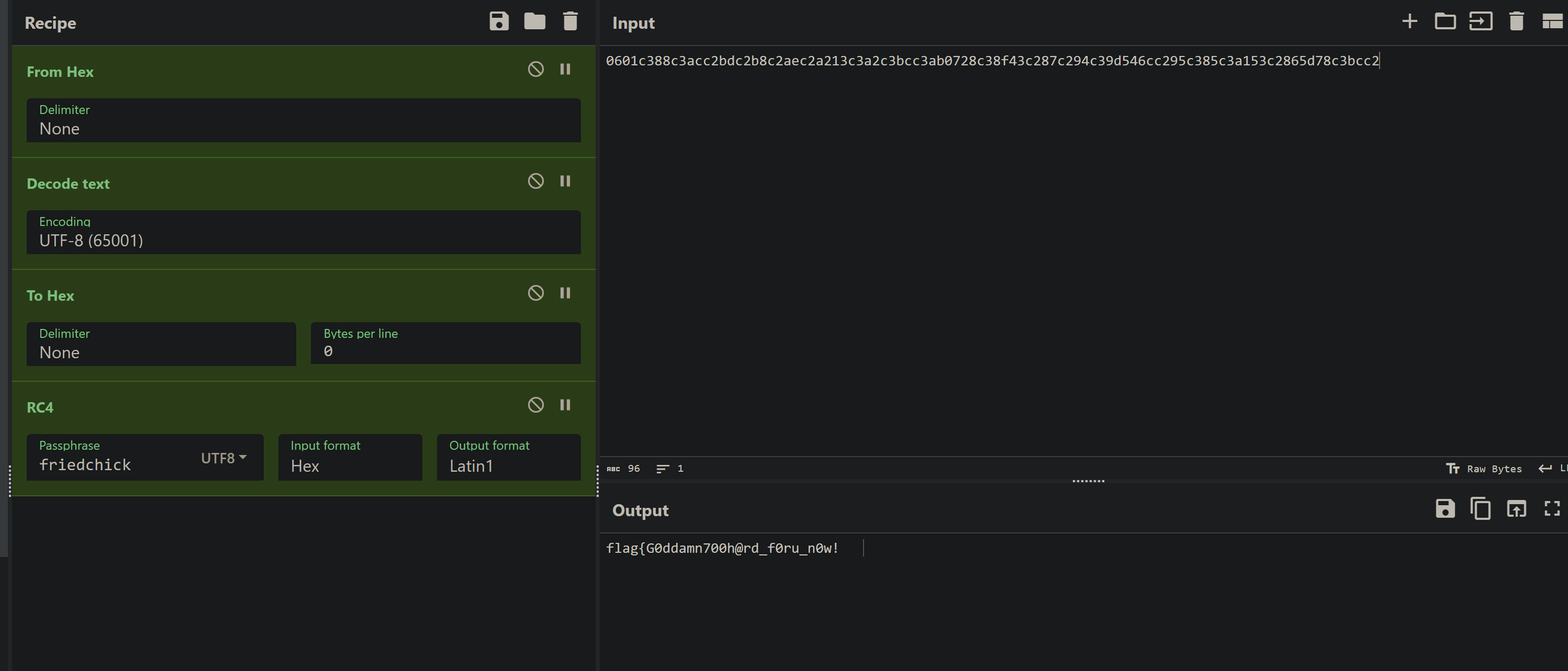
flag因为出题人脚本有问题,故不全。
Week4
iwannarest
没什么特别的,跟一跟就可以了,一个TEA类型的算法
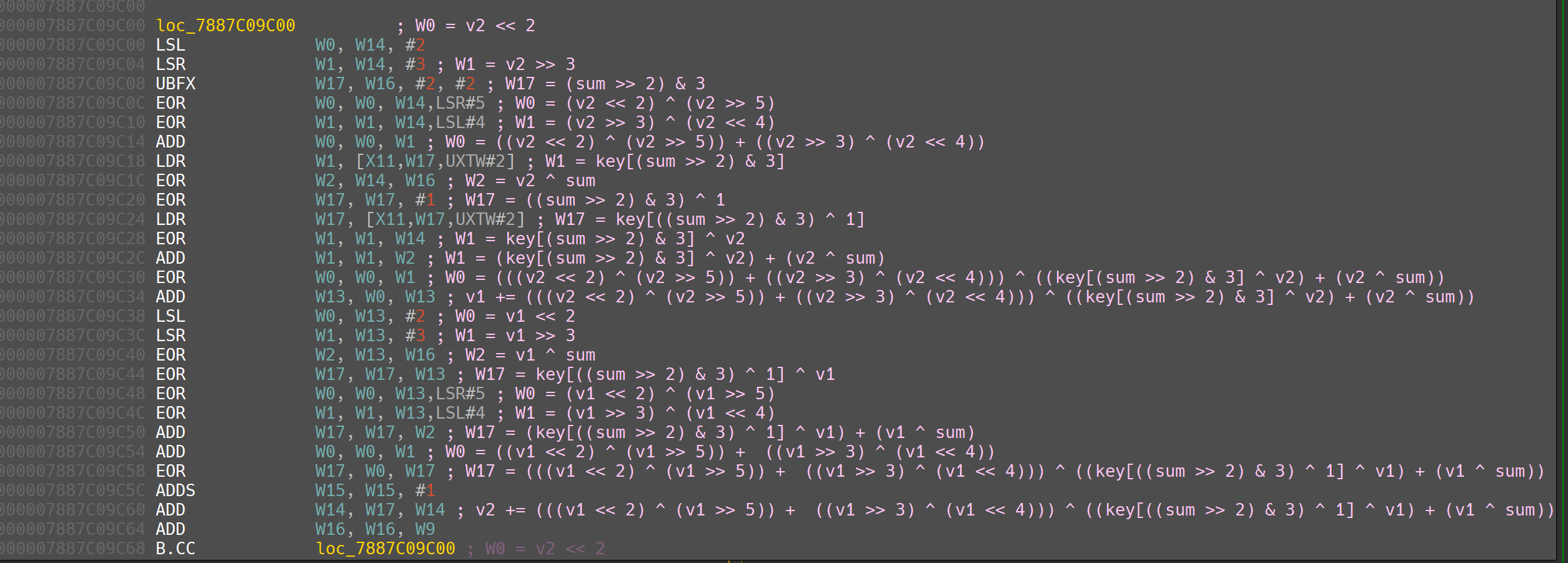
对应加密
1 | |
对应解密
1 | |
简单的跨栏
Java层RC4,Native层变表64,直接静态手撕

Week5
Java层有两个反调试,patch一下即可。
然后主要逻辑都是在Native层,函数是动态注册的,所以名字找不到。不过关键地方也很容易看到,这里用了一个indirectJump混淆,即通过跳转寄存器来混淆。动态调试一下,比较容易看到关键地方。

显然这里将前8字节拆分为两个4字节分别存入w10 w9寄存器,还有魔数0x9E3779B9,大体可以猜测出是TEA类的算法加密,然后继续跟一下就能看到完整的加密流程

Key、密文什么的也很容易拿到,直接搓逆脚本
1 | |